- Home
-
Product
Sectigo
Extended Validation(EV)SSL Organization Validation(OV)SSL Domain Validation(DV)SSL Wildcard SSL Multi-Domain SSL Single-Domain SSL Compare Certificates - About Us
- Contact Us
SigningHub Advanced Electronic Signatures (AES) Are:
- uniquely linked to the signatory;
- capable of identifying the signatory;
- created using means that the signatory can maintain under their sole control; and
- linked to the data to which it relates in such a manner that any subsequent change of the data is detectable.
SigningHub implements such signatures using standard PKI cryptography. Each user has a unique PKI signing key and associated digital certificate. The certificate acts as the person’s “digital identity” and is embedded in each signature they create – thereby securely binding the signer’s identity to their signed documents. The signing key which is used to create the signature is private and remains under the sole control of the owner, only accessible after appropriate authentication and authorisation checks.
SigningHub AES Are Secure, High-Trust And Easy To Use. We Support:
Remote Signing
User signing keys are held server-side in a secure HSM or encrypted DB
Local Signing
User’s signing key is held locally on a smartcard, USB token or secure software container
Mobile Signing
User’s signing key is held in the mobile’s “Secure Element” hardware
How To Check If An Aes Was Ued:

Signatures
For signed PDF documents you can easily determine if an AES was used by opening the document in Adobe® Reader as shown below. You can see who signed from the blue bar, or by simply clicking on the e-signature appearance to see the pop-up details highlighted below. You should see the name of the real person who created this signature if AES are being used, if instead you see the service provider’s name here then only basic e-signatures are being used and not AES!

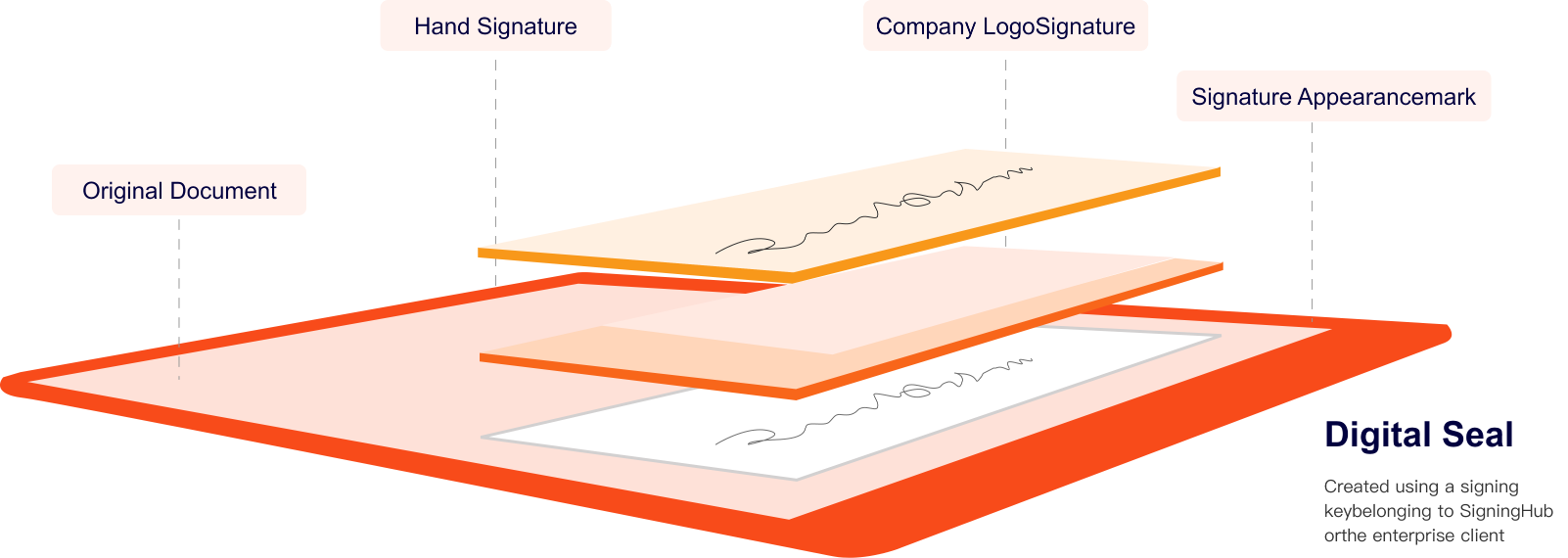
See What’s Inside A Basic Signature:
After the user has made their e-signature appearance mark on the document, behind the scene SigningHub protects the document by locking it with an advanced e-Seal, using a key that it owns or that belonging to the enterprise account holder (e.g. bank, office, shop etc).
SigningHub Works With Certificates From:
Global Online CAs
SigningHub can obtain Adobe-approved AATL certificates automatically in real-time from our partner CAs in the remote signing use case
SigningHub built-in CA
Set-up your own enterprise-branded CAs inside SigningHub to issue certificates to your users
National/Local CAs
Use any CA within your organisation, industry or country e.g. your national eID CAs
Our Online Qualified CA Partners
Set-up your own enterprise-branded CAs inside SigningHub to issue certificates to your users
External Qualified CAs
Use any CA within your organisation, industry or country e.g. your national eID CAs
